呜呜呜终于更新博客了,不摸了不摸了。周末玩了下美团CTF,可惜被轮子影响思路了,结束还是0解,之后做出来了。wp这边还是放出来吧。
ezdct-svd
Description
Analyze
开局一张图

根据题目名ezdct-svd就可以知道是dct的频域隐写,然后hint.txt为
我们找到了用于嵌入水印的脚本文件hide.py中其中的三行(这三行并不挨着):
watermark = cv2.imread('qrcode.bmp', cv2.IMREAD_GRAYSCALE).flatten() > 128
block_shape = (8, 8)
Sigma[0] = (Sigma[0] // 30 + 0.5 * watermark[i] + 0.25) * 30最后那句可以在invisible-watermark/dwtDctSvd.py at main · ShieldMnt/invisible-watermark (github.com)这找到相关源码,解量化的方法就是 int ((s[0] % scale) > scale * 0.5),思路就结束了,所以说图片先分块,然后用dct变换后再svd分解,取矩阵的最大特征值后解量化即可,据此写脚本得到
import matplotlib.pyplot as plt
import cv2
import numpy as np
def infer_dct_svd(frame):
_block = 8
res = []
row, col = frame.shape
for i in range(row//_block):
for j in range(col//_block):
block = np.float32(frame[i*_block : i*_block + _block,j*_block : j*_block + _block])
_DCT = cv2.dct(block)
u,s,v = np.linalg.svd(_DCT)
# print(s[0])
score = int ((s[0] % 30) > 30 * 0.5)
res.append(score)
return np.array(res)*255
wm_length = 64*64
pic = cv2.imread('embedded.bmp')
count = 0
R = pic[:,:,2]
r = infer_dct_svd(R)[:64*64].reshape(64,64)
plt.imshow(r)
plt.show()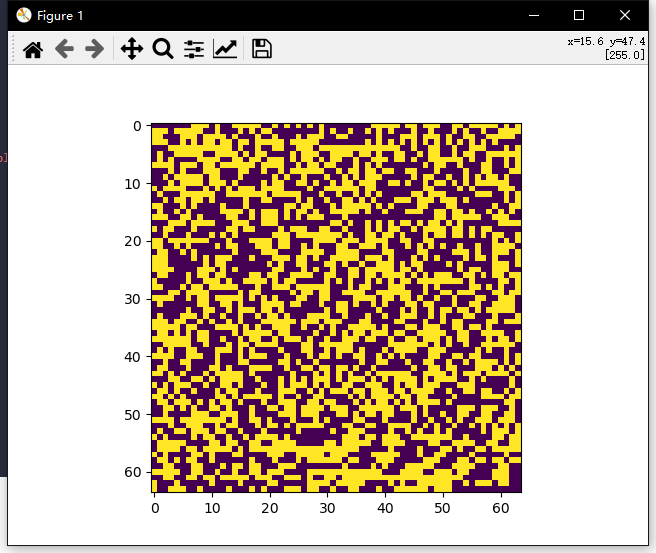
其实这边有三个图层,但是一般都是先从r图层开始,这里可以很清楚的看见最上面有一长串的黑值,且长度为7,找到下一处长度为7的黑条,数了下长度为37,而37*37也正是二维码的尺寸,修改size即可得到flag二维码
import matplotlib.pyplot as plt
import cv2
import numpy as np
def infer_dct_svd(frame):
_block = 8
res = []
row, col = frame.shape
for i in range(row//_block):
for j in range(col//_block):
block = np.float32(frame[i*_block : i*_block + _block,j*_block : j*_block + _block])
_DCT = cv2.dct(block)
u,s,v = np.linalg.svd(_DCT)
# print(s[0])
score = int ((s[0] % 30) > 30 * 0.5)
res.append(score)
return np.array(res)*255
wm_length = 64*64
pic = cv2.imread('embedded.bmp')
count = 0
R = pic[:,:,2]
r = infer_dct_svd(R)[:37*37].reshape(37,37)
plt.imshow(r)
plt.show()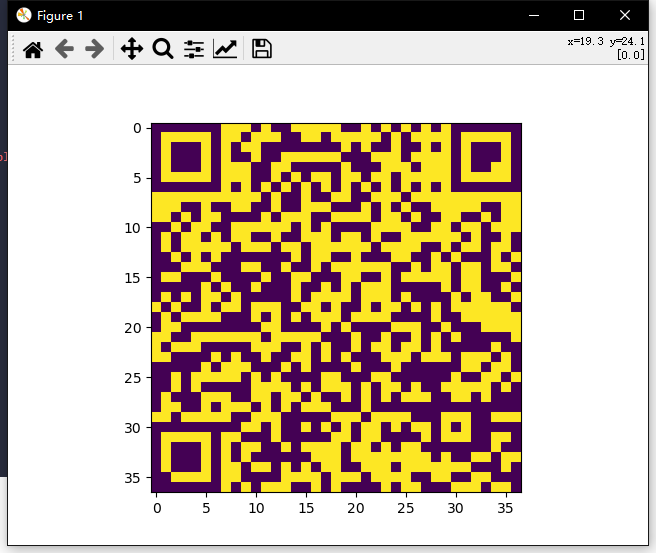
flag
flag{4a8a4732-df32-415d-9945-d5ce0a16a0d1}