单身狗的七夕——安恒8月赛

呜呜呜人人都有npy就我没有
签到
Description
9张撕碎的二维码
Analyze
是原题,谷歌搜图得flag
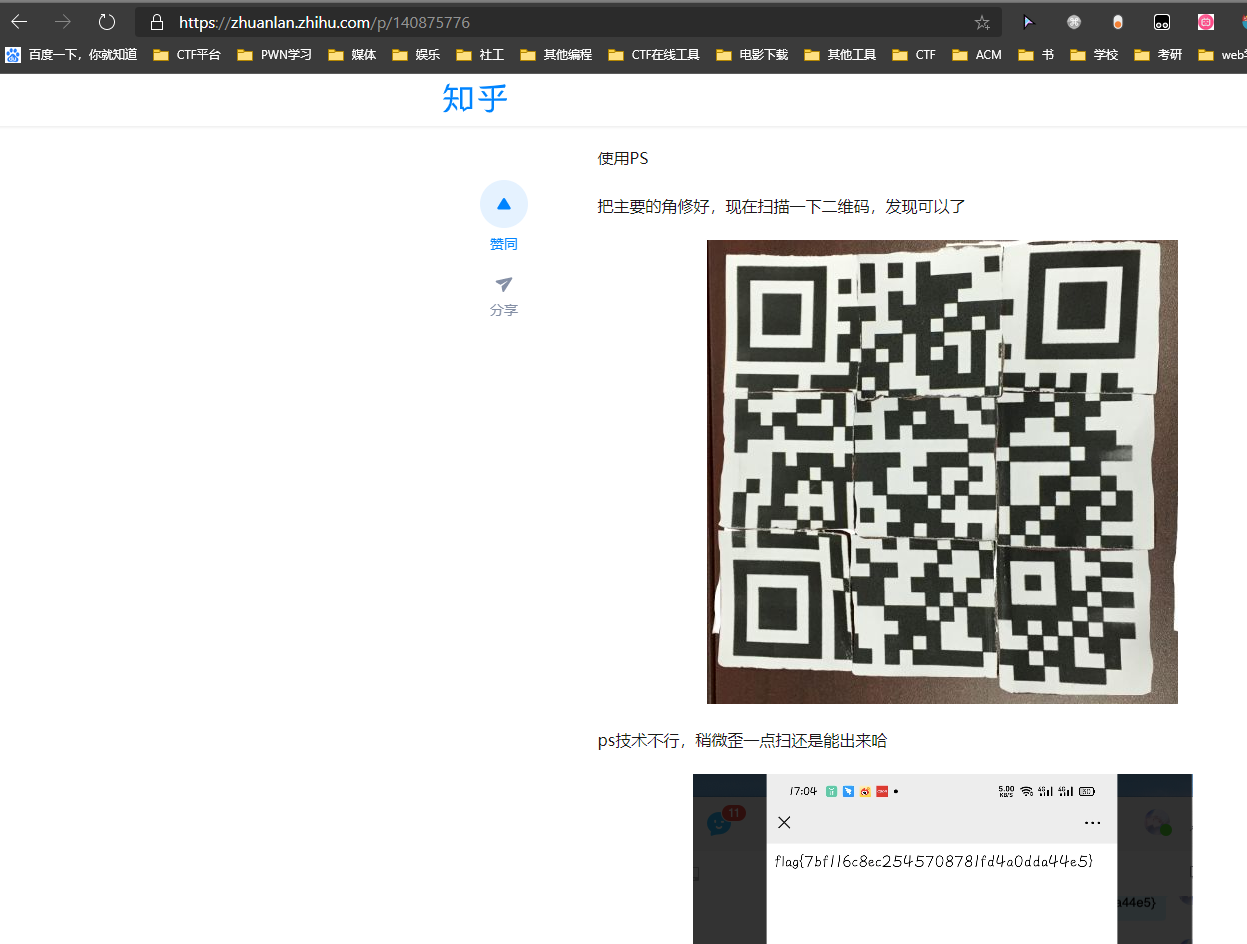
flag
flag{7bf116c8ec2545708781fd4a0dda44e5}eeeeeeeasyusb
Description
神秘代码:DYcbU-gQz_TZCBjh8rID/JmTjTw
Analyze
vim后发现有空字符,猜测是宽字节隐写,https://tools.miku.ac/zero_width_space_encrypt/
是44m4n(然而好像没有什么卵用)
然后这串神秘代码,因为自己曾经出过类似的题,是百度云盘的尾链接,所以猜测这个也是某个云盘的链接,最后找到是坚果云https://www.jianguoyun.com/p/DYcbU-gQz_TZCBjh8rID提取密码是JmTjTw,两个流量文件,一个键盘一个鼠标流量,网上脚本只能解键盘的,鼠标的最后得修改提取数据位置稍微改下脚本(ps:hint对应1 3 5字节,也就是这三个字节为关键数据区
#!/usr/bin/env python
# coding=utf-8
nums = []
keys = open('data.txt','r')
posx = 0
posy = 0
res = open('res.txt','a')
for line in keys:
try:
x = int(line[4:6],16)
y = int(line[8:10],16)
if x > 127 :
x -= 256
if y > 127 :
y -= 256
posx += x
posy += y
btn_flag = int(line[0:2],16) # 1 for left , 2 for right , 0 for nothing
# print(line[4:6])
if btn_flag == 1 :
print(posx,posy)
res.write(str(posx)+' '+str(posy))
res.write('\n')
except:
pass
res.close()跑出part1,再旋转镜像一下得到
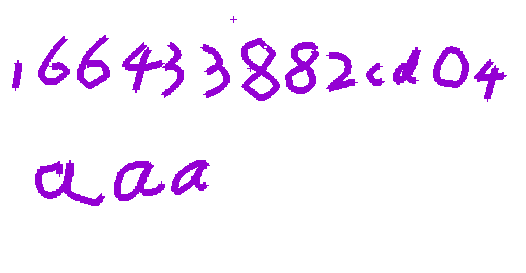
part2直接脚本嗦出来:
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
nums = []
keys = open('data.txt')
for line in keys:
if len(line)!=17: #首先过滤掉鼠标等其他设备的USB流量
continue
nums.append(line[0:2]+line[4:6]) #取一、三字节
keys.close()
output = ""
for n in nums:
if n[2:4] == "00" :
continue
if n[2:4] in normalKeys:
if n[0:2]=="02": #表示按下了shift
output += shiftKeys [n[2:4]]
else :
output += normalKeys [n[2:4]]
else:
output += '[unknown]'
print('output :n' + output)output :n056<F2><F2><F2><F2><F3><F2><F2><F2><F3><F3>4<F2><F2><F2><F2><F2><F2><F2><F2><F3><F3>29<F2><F2><F2><F2><F3><F2><F2><F2><F2><F3>522<F2><F2><F2><F2><F3>然后根据前面part1有16位,part2应该也有16位,已知的9位以及35个F2,F3,易得5个F2,F3为一个字符,易得为培根密码,解密后得
056bd4ad29bb522b
flag
166433882cd04aaa056bd4ad29bb522b双重图格
Description
Analyze
解压后一个png一个jpg还有一个hint表格,png文件尾不对,多了一段fctl的数据格,hint的表格打开后没有东西,按照常理搜下空格,发现

Insert:OFFSET 28354h,可能是说把多出来的数据块放到那个位置,放完后图片好像没什么变化,再看看图片,有fdAT和IDAT,这是apng的一个特征,把他丢到浏览器中(ps:个别浏览器可能不支持apng),发现有东西一闪而过,用王者手速我给截屏下来了

这个是个DotCode,用在线扫描器扫描后得到 U2FsdGVkX1/mLyhDqehTlmxmPoamVfr7h1El3iWRVvuJQodh1HvxMeQ2F8lgHfXzq70N4U/ZcjYtjLbXE8HRmw==
然后jpg处理,直接丢不进去010editer,给我卡傻了,然后用hxd搜索jpg的文件尾,发现两个文件尾
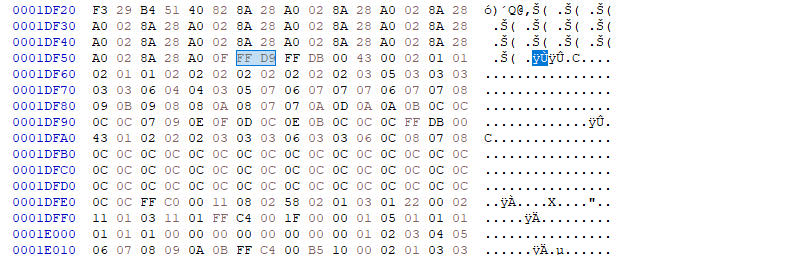
在图所示这块加上文件头,foremost后得到

在和一开始的图片,把两个二维码扣下来,再稍微补一下掩码得


xor一下

扫描得key:apngisamazing
在线网站解密得flag
flag
DASCTF{b12e6674e844486d20d24793809ae38a}标错的字符
Analyze
猜都猜到肯定要被非预期打(预期解打完比赛我再试试)
非预期为寻找文件的格式,就搜索_x(数字字母),然后一个个看,很容易找出哪个标错了,然后发现编号7,17,77,177,777,1777,7777充满7的意志的7个号出现了错误,这些字母是x9sa5v0,md5得到flag
flag
287fe711b6c25ec4352df516e7f8cc33