今天摸了仨网鼎白虎的misc
2020网鼎白虎签到摸鱼记
MISC
hidden
Description
NULL
Analyze
开局一张图

有效信息后有zip文件,foremost后zip爆破密码得到密码1235,解压得到半个二维码

然后crc错误易得是高度错误,修复后扫码得到flag
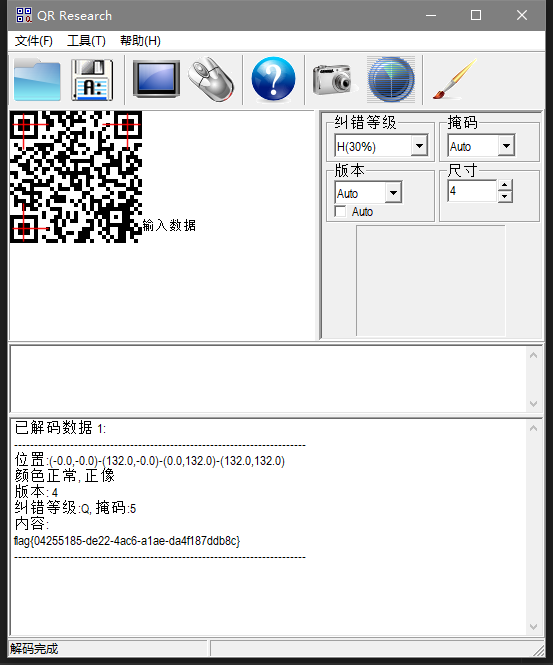
flag
flag{04255185-de22-4ac6-a1ae-da4f187ddb8c}hack
Description
NULL
Analyze
首先下载文件后,是一个明文破解zip,找到sqlmap1.4下载后明文破解,得到一个0day.zip和xor,xor易得是用xortools破解,得到
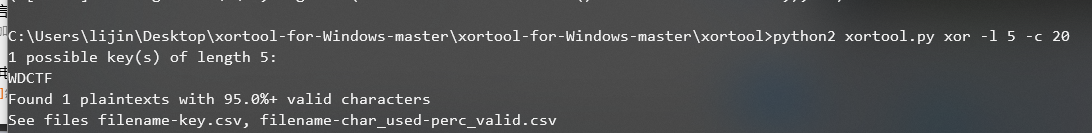
里面数据是
This is a hacking kit that can break into satellite equipment with one click. It has a million 0day. If you want to use this tool, please pay my bank cardXOR.
password:qw91!25fzd$@!
Beautiful is better than ugly.
Explicit is better than implicit.
Simple is better than complex.
Complex is better than complicated.
Flat is better than nested.
Sparse is better than dense.
Readability counts.
Special cases aren't special enough to break the rules.
Although practicality beats purity.
Errors should never pass silently.
Unless explicitly silenced.
In the face of ambiguity, refuse the temptation to guess.
There should be one-- and preferably only one --obvious way to do it.
Although that way may not be obvious at first unless you're Dutch.
Now is better than never.
Although never is often better than *right* now.
If the implementation is hard to explain, it's a bad idea.
If the implementation is easy to explain, it may be a good idea.
Namespaces are one honking great idea -- let's do more of those!
Beautiful is better than ugly.
Explicit is better than implicit.
Simple is better than complex.
Complex is better than complicated.
Flat is better than nested.
Sparse is better than dense.
Readability counts.
Special cases aren't special enough to break the rules.
Although practicality beats purity.
Errors should never pass silently.
Unless explicitly silenced.
In the face of ambiguity, refuse the temptation to guess.
There should be one-- and preferably only one --obvious way to do it.
Although that way may not be obvious at first unless you're Dutch.
Now is better than never.
Although never is often better than *right* now.
If the implementation is hard to explain, it's a bad idea.
If the implementation is easy to explain, it may be a good idea.
Namespaces are one honking great idea -- let's do more of those!密码为qw91!25fzd$@!,解压后是MZWGCZ33MY2DMODBGU2DCLJTGJSWKLJUMQZTOLLCHAZDKLJQMI4GCMRQGU2TQNJSGN6Q====的base32,解密后得到flag。
flag
flag{f468a541-32ee-4d37-b825-0b8a20558523}密码柜
Description
NULL
Analyze
夏风师傅的取证题,十分的硬核和复杂。首先打开一个vmem文件和Database.kdbx文件,kdbx文件使用KeePass软件读取,需要一个密码,应该是在win10的vmem中找。于是取证大师一把梭(其实也可以使用volatility,但是十分麻烦,还是取证大师一把梭简单),数据恢复后得到
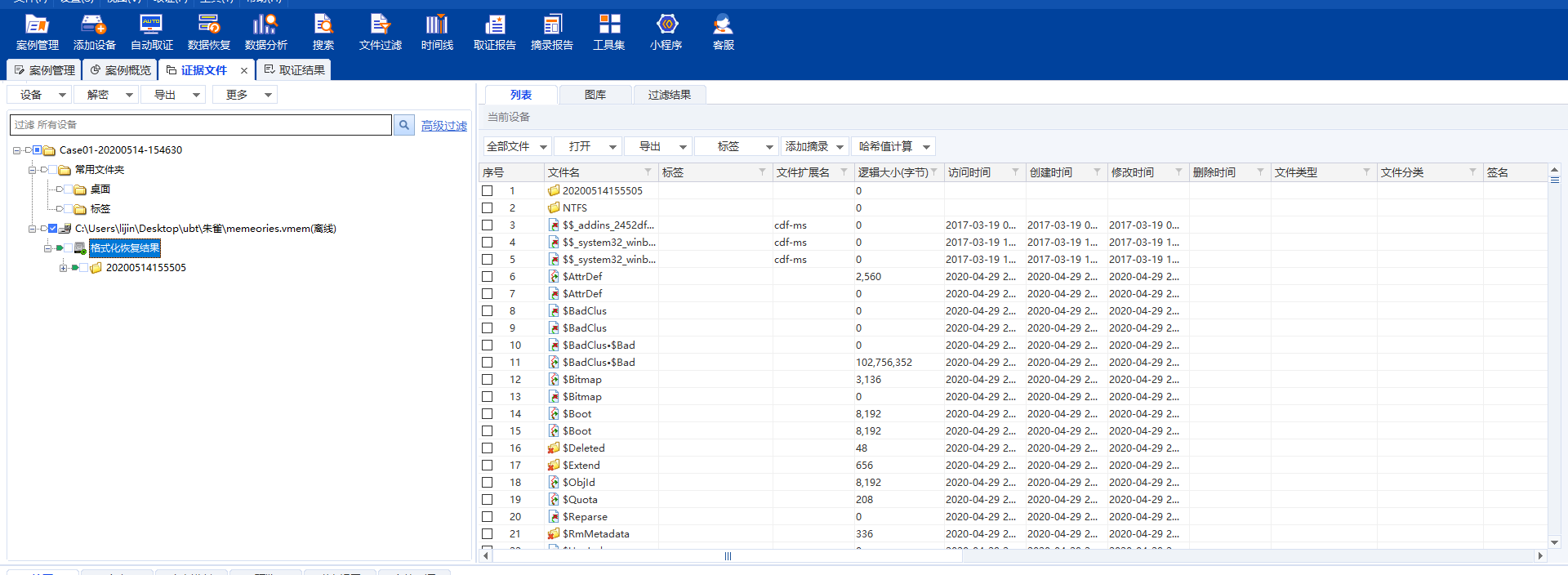
查找txt有个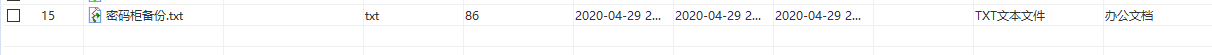
打开后是
密码柜的密码可不能忘了,毕竟那里面存着我最重要的东西
而且我走哪都要带着它
6s4mxkhvge用这个KeePass的密码解密,得到
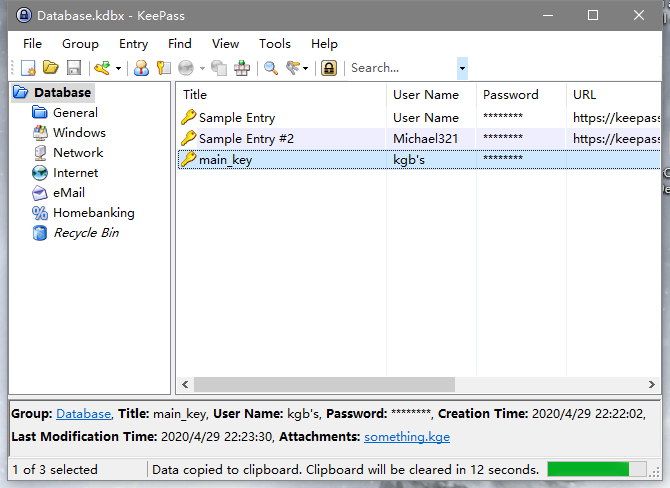
这也是一种加密,密钥就是main_key,里面有一个Advanced,可以把里面一个something.kge文件导出,密码就是main_key:XLlArBkn。导出后再使用KGB Archiver对数据进行解压,得到一个BitLocker硬盘,但是没有密钥文件,猜测还是再vmem的win10镜像中,使用Elcomsoft Password Recovery对vmem进行提取,得到
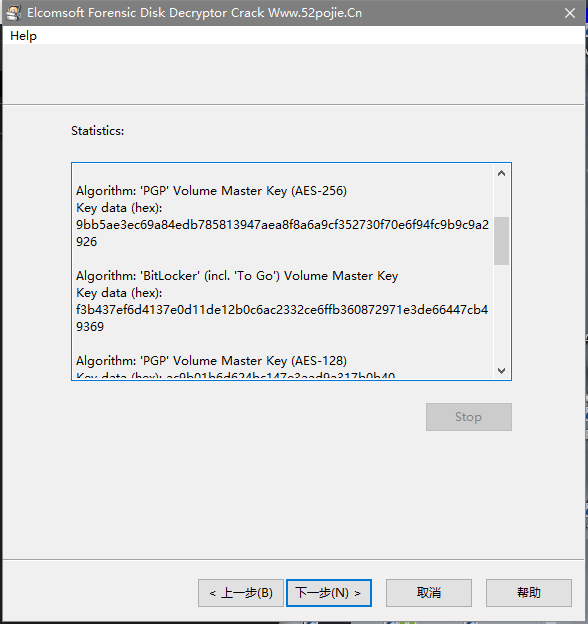
导出后挂载解压的BitLocker硬盘,然后再用Elcomsoft Password Recovery对用刚刚导出的密钥对BitLocker硬盘进行解密
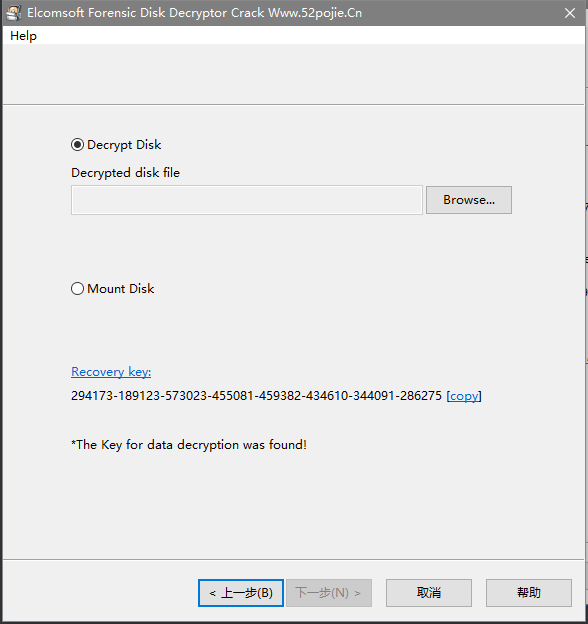
解密的key就是294173-189123-573023-455081-459382-434610-344091-286275,输入密钥,进入硬盘
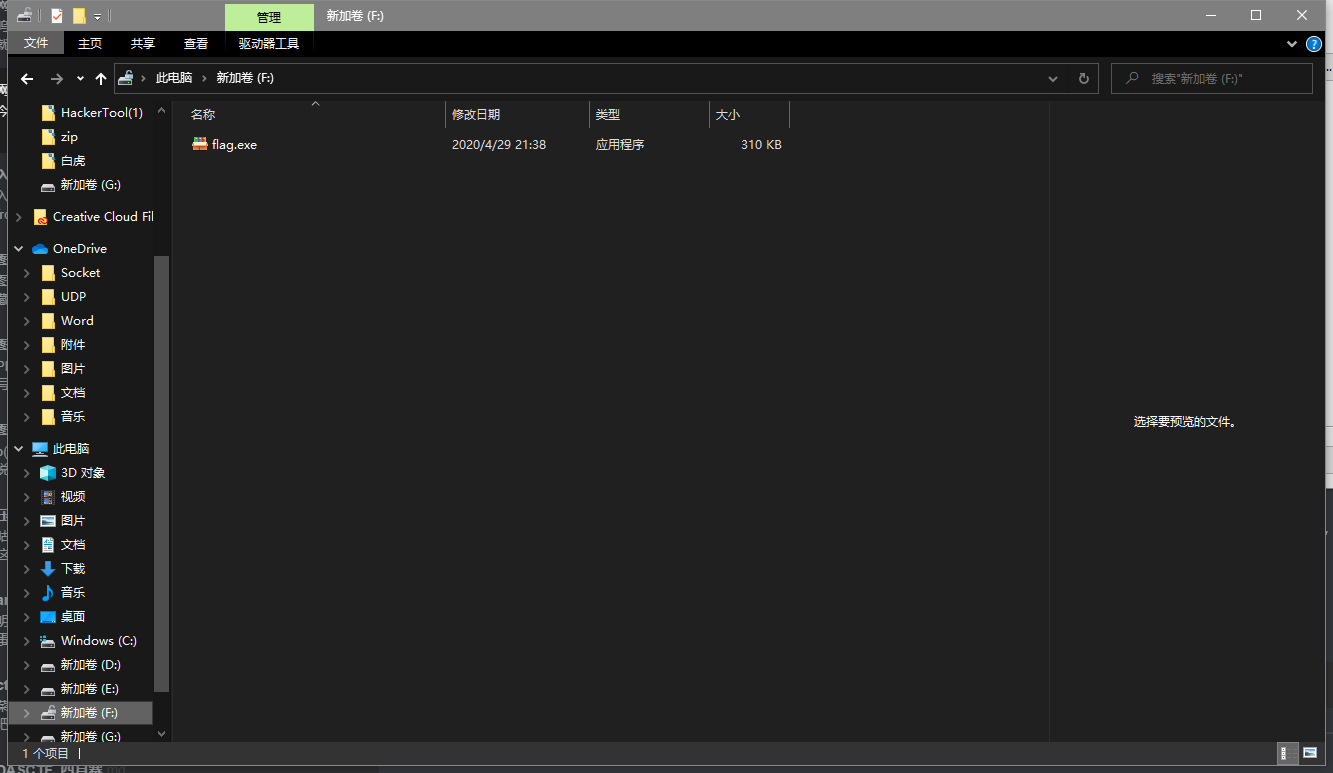
里面是一个自解压程序,打开这个程序后发现
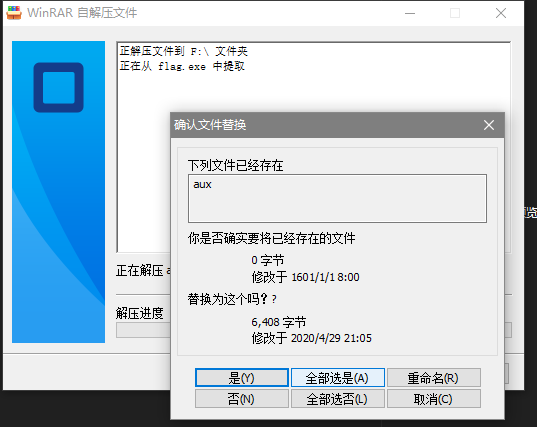
aux是windows里的一种保留字,强行保存也打不开文件,所以我们对其进行重命名,之后用命令行对其进行cat操作
是一个PNG图片,那就加一个后缀名打开,得到flag

flag
flag{700cf8df-0444-46a4-afd2-22dcce208a67}